The media has been awash with sensationalist stories of ‘cyber attacks on the NHS’.
This is, of course a misrepresentation of the facts.
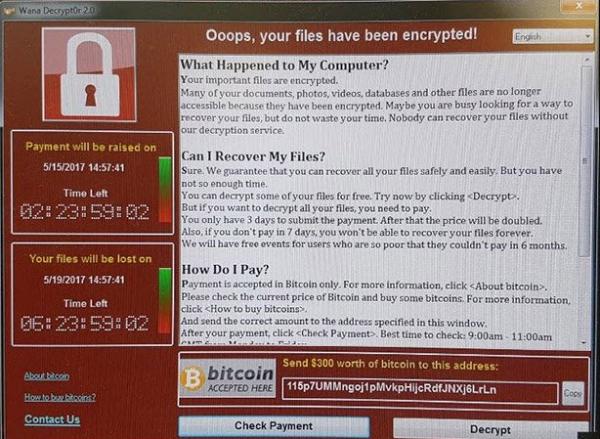
NHS trusts have fallen victim of a piece of insidious ‘ransomware’ that, according to Europol – and reported on the BBC News website here – have infected more than two hundred thousand victims in one hundred and fifty countries.
Other reports suggest as many as nine million computers in nearly two hundred countries.
The malware – known as ‘Wannacry exploited a ‘back door’ known as ‘EternalBlue’ that the New York Times described as “a vulnerability that was discovered and developed by the National Security Agency (NSA).”
Microsoft issued security patches to its current operating systems a few months ago when ‘EternalBlue’ had been leaked by a hacking group known as the Shadow Brokers.
Of course, as we have reported here in the past, older operating systems such as Windows XP, Server 2003 and Vista are no longer publicly supported, and so no fixes were offered.
On Saturday May 13th Microsoft took the unexpected step of releasing an ‘out of bounds patch’ for unsupported operating systems such as Windows XP and Server 2003 meaning that people now are able to patch rather than having to attempt upgrades to newer system in order to be secured against this worm.
Sunday’s British newspapers reported that a British InfoSec specialist – Malware Tech – had halted the initial attack by identifying and activating a ‘kill switch’ that sought a hitherto unregistered domain.
Somewhat worryingly, ‘Wannacry2’ has been identified ‘in the wild’ that has no such kill switch.
The threat remains.
Lessons to be learned:
Ensure your key data files are backed up onto a separate device, or in ‘the cloud’ – if your machine is encrypted by malware (and I know people who’ve fallen foul of ransomware in the past) then you should be able to restore from data from backups, once a new, supported, operating system is installed.
Ensure your operating systems are still actively supported. Support for Windows XP ceased in April 2014 and Windows Vista last month (April 2017)
Ensure that you install all security patches promptly. One organisation we work with insists that all its PCs are left powered on overnight every Tuesday night for operating system upgrades, and security patches are rolled across the network as soon as they arrive.
And, of course, never open emails from unexpected sources, and research any links before clicking on them.
